Uploading findings from a file
Opus supports adding uploading findings in several formats, and custom format as a CSV
To upload findings from a custom CSV file into Opus you'll need to have it formatted with specific fields to match the fields in Opus to allow Opus to map the findings and enrich them.
Uploading file:
1. Navigate to Risks:
-
On the top right hand side click Import
-
In the first drop-down list select "Custom Finding Source"
-
Under the "finding sources" section, click on "Custom finding source". and select Generic CSV
-
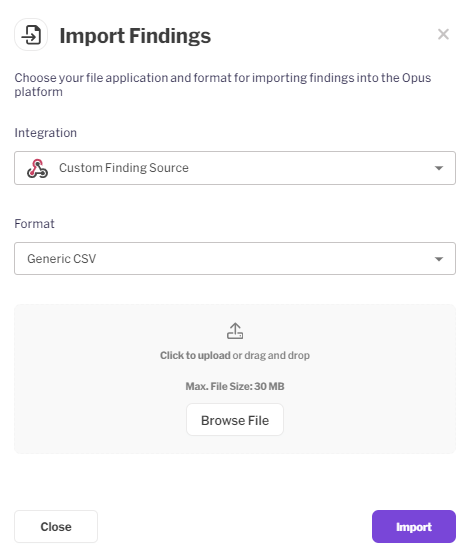
Browse or drag & drop a single file of your choice (up to 30MB) and click Import
See the Next Section related to the possibilities data fields and their mapping
Data Scheme for Ingestion:
The following Shema described mandatory fields and their usage within Opus
Schema Attribute Breakdown
Field | Type | Value | Description |
|---|---|---|---|
type | String | Type of the event | Acts as the rule generator of the finding. Group by risk is grouped around this value. |
externalId | String | Unique id of the finding | Important for resolving existing findings in Opus and for avoiding creating duplications. |
title | String | Title for finding page | The title of the finding |
description | String | Description for finding page | The description of the finding |
createdAt | datetime | Creation date of the issue on the finding source. 2024-01-30T13:12:06.729Z | The finding detection time |
resourceId | String | Unique id of the resource (e.g., Aws ARN, Azure URI, Gcp Id, Hostname) | Important for cloud to code purposes, ensure to provide the exact vendor id. For code, provide the code path. |
resourceName | String | Name of the resource | Name of the resource |
resourceType | String | Type of the resource (e.g., AwsEc2Instance, AzureVm...) | Flexible value, logos are loaded according to Opus reserved types (See below for a complete list of Resource Types) |
severity | Enum | Severity of the issue - Informational, Low, Medium, High, Critical | Provides the sensor score as an input for the risk score computation. |
cloudProvider | String | Provider of the issue (e.g., AWS, AZURE, GCP, Github, GitLab, On-Premises) | Cloud or code provider vendor |
findingSource | String | Source of the finding (e.g., Orca, Wiz, Snyk) | Your desired source name, with the ability to filter by it. |
workspaceId | String | Cloud account unique id (e.g., Aws account id, Azure subscription id, Gcp project id, Github/Gitlab repo id) | Used for matching the finding to the proper workspace and for the correct Business Unit/service. |
category | String | Category of the finding (e.g., Vulnerabilities, Code Vulnerability, Data Protection...) | Flexible text, with the ability to filter by it. |
externalStatus | Enum | External status on finding source (Open, Suppress, Resolved) | Incase finding with the same externalId exist in Opus with externalStatus Resolved the finding is resolved in Opus. |
layer | Enum | Detection layer of the finding (e.g., Runtime, Artifact, Code, On-Premises) | Detection layer of the finding. |
findingType | Enum | Type of the finding (e.g Secrets, SCA, SAST, IAC Security, Container Vulnerability, Cloud Vulnerability, On-Premises Vulnerability, | Type of the finding. |
Example #1 - Cloud Layer
"type","title","description","createdAt","resourceId","resourceName","resourceType","severity","cloudProvider","findingSource","workspaceId","category","externalId","externalStatus","layer","findingType","resourceTags__Owner","resourceTags__Env"
"standards/aws-foundational-security-best-practices/v/1.0.0/S3.2","S3 buckets allow public read access","This AWS control checks whether your S3 buckets allow public read access by evaluating the Block Public Access settings, the bucket policy, and the bucket access control list (ACL).","2023-09-10T11:25:53.000Z","arn:aws:s3:::802256041567-bucket-8","bucket-8","AwsS3Bucket","HIGH","AWS","MySourceName","802256041567","Data Protection","arn:aws:securityhub:us-east-1:802256041567:security-control/S3.2/finding/80225604156701","Open","Runtime","Cloud Misconfiguration","[[email protected]](mailto:[email protected])","Dev"Example #2 - Code Layer
"type","title","description","createdAt","resourceId","resourceName","resourceType","severity","cloudProvider","workspaceId","findingSource","externalId","externalStatus","category","layer","findingType"
"aws_access_key_id","Possibly active secret","Possibly active secret\nPath: terraform/aws/ec22.tf\nStart line: 15\nEnd line: 15 \n Blob SHA: 4e7b92c3e89b5e7229a208379fc465b03749ec6c\nCommit SHA: 1e25f4212a1c4e176bb122531a7ebd5969815367\nRepository Info: \nname: OpusSecurityLab/terragoat","2024-01-09T15:13:31Z","OpusSecurityLab/terragoat/terraform/aws/ec22.tf","terraform/aws/ec22.tf","CodeFile","MEDIUM","Github","OpusSecurityLab/terragoat","Github Advanced Security","2","Open","Secerts","Code","Code Vulnerability"Update Finding Status
Opus provides the functionality to synchronize the finding status with changes occurring in the external source. By uploading an update event to Opus, and adjusting the externalStatus field to the value 'Resolved', the status within Opus will be updated to reflect this change.
Example 3- Resolved Status Update
"type","title","description","createdAt","resourceId","resourceName","resourceType","severity","cloudProvider","findingSource","workspaceId","category","externalId","externalStatus","layer","findingType","resourceTags__Owner","resourceTags__Env"
"standards/aws-foundational-security-best-practices/v/1.0.0/S3.2","S3 buckets allow public read access","This AWS control checks whether your S3 buckets allow public read access by evaluating the Block Public Access settings, the bucket policy, and the bucket access control list (ACL).","2023-09-10T11:25:53.000Z","arn:aws:s3:::802256041567-bucket-8","bucket-8","AwsS3Bucket","HIGH","AWS","MySourceName","802256041567","Data Protection","arn:aws:securityhub:us-east-1:802256041567:security-control/S3.2/finding/80225604156701","Resolved","Runtime","Cloud Misconfiguration","[[email protected]](mailto:[email protected])","Dev".
Supported Rescource Types |
|---|
AccessRoleBinding AwsAccount AwsAsg AwsAthenaWorkGroup AwsAutoScalingAutoScalingGroup AwsAutoScalingGroup AwsCertificate AwsCloudFormationStack AwsCloudFront AwsCloudTrail AwsCloudTrailTrail AwsEc2EbsSnapshot AwsEc2EbsVolume AwsEc2ElasticIpAddress AwsEc2Elb AwsEc2Elbv2 AwsEc2Instance AwsEc2LaunchTemplate AwsEc2NetworkAcl AwsEc2NetworkInterface AwsEc2SecurityGroup AwsEc2Snapshot AwsEc2Subnet AwsEc2Volume AwsEc2Vpc AwsEc2VpcEndpoint AwsEcrContainerImage AwsEcrRepository AwsEcsCluster AwsEcsContainerInstance AwsEcsService AwsEcsTaskDefinition AwsEfsAccessPoint AwsEfsFileSystem AwsEksCluster AwsEksNodegroup AwsElbv2LoadBalancer AwsGlueDataCatalog AwsIamAccessKey AwsIamGroup AwsIamManagedPolicy AwsIamPasswordPolicy AwsIamPolicy AwsIamRole AWSIAMRole AwsIamUser AwsKmsKey AwsLambdaFunction AwsRdsDbCluster AwsRdsDbClusterSnapshot AwsRdsDbInstance AwsRdsDbInstanceGabay AwsRdsDbInstanceSnapshot AwsRdsDbSnapshot AwsRegion AwsRoute53HostedZone AwsS3Bucket AwsSecretsManagerSecret AwsSnsSubscription AwsSnsTopic AwsSqsQueue AwsSsmAssociationCompliance AwsSubnet AwsSystemsManagerParameter AwsUser AwsVpc AzureAcrContainerImage AzureAcrImage AzureComputeVm AzureContainerRegistry AzureDisk AzureFunction AzureNetworkInterface AzureNetworkSecurityGroup AzureNetworkSecurityGroupRule AzureNetworkWatcher AzurePostgresDbServer AzureRoleAssignment AzureSotrageAccount AzureSqlDbServer AzureStorageAccount AzureStorageContainer AzureSubscription AzureUser AzureVNet AzureWebAppService CloudFormationFile CodeFile Container Dockerfile GcpGcrContainerImage GcpGcrImage GcpIamServiceAccount GcpNewDomain GcpSqlInstance GcpStorageBucket GcpSubnet GcpVmInstance GcpVpc GcpVpcSubnet PackageManager TerraformFile URL WorkStation |
Updated 5 days ago
